Docs Home → Atlas App Services
Google Authentication
On this page
Overview
The Google authentication provider allows users to log in with their existing Google account through Google Sign-In. When a user logs in, Google provides Atlas App Services with an OAuth 2.0 access token for the user. App Services uses the token to identify the user and access approved data from Google APIs on their behalf.
The following diagram shows the OAuth logic flow:
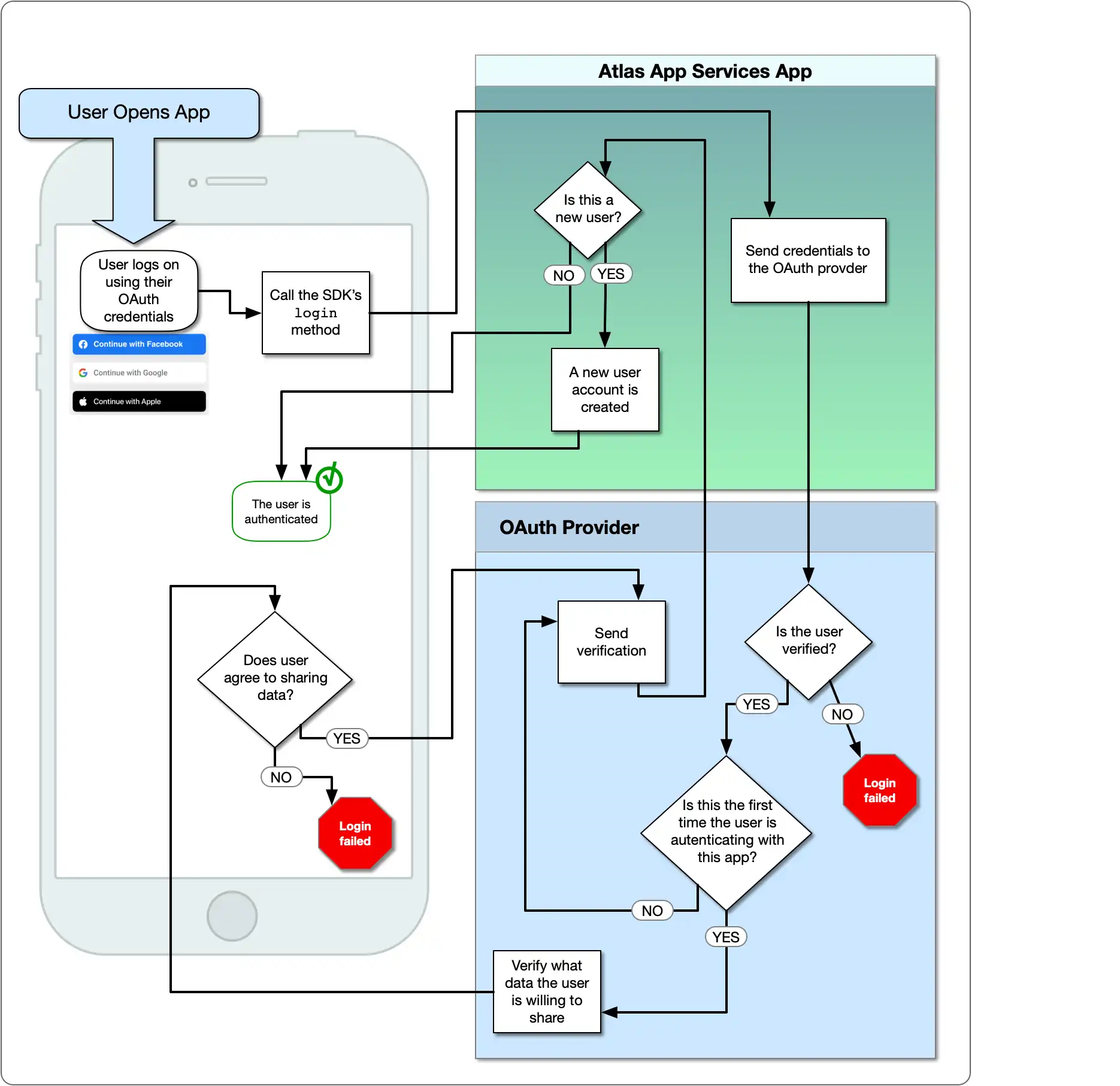
Set Up a Project in the Google API Console
You must set up a project in the Google API Console before you configure Google Authentication in App Services. Follow the SDK-specific steps to set up Google Authentication in the Google API Console.
The Google authentication provider requires a project in the Google API Console to manage authentication and user permissions. The following steps walk through creating the project, generating OAuth credentials, and configuring the provider to connect with the project.
Create a Project in the Google API Console
Follow Google's official guide to create a new GCP project.
Generate OAuth Client Credentials
Follow Google's support guide on Setting up OAuth 2.0 for your project.
Configure the Google Authentication Provider
To connect your GCP project to App Services add the OAuth 2.0 Client ID and Client Secret you generated in the previous step to your authentication provider configuration.
Configure in App Services
The Google authentication provider has the following configuration options:
Field | Description | |
|---|---|---|
Client ID config.clientId | Required. An OAuth 2.0 Client ID for your project in the Google API Console. See Set Up a Project in the Google API Console for information about setting up OAuth Credentials for your GCP project. | |
Client Secret secret_config.clientSecret | Required. The name of a Secret that stores an OAuth 2.0 Client Secret for your project from the Google API Console. See Set Up a Project in the Google API Console for information about setting up OAuth Credentials for your GCP project. | |
Metadata Fields metadata_fields | Optional. A list of fields describing the authenticated user that your application will request from the Google Identity API. All metadata fields are omitted by default and can be required on a field-by-field basis. Users must explicitly grant your app permission to access each required field. If a metadata field is required and exists for a particular user, it will be included in their user object. To require a metadata field from an import/export
configuration file, add an entry for the field to the
| |
Redirect URIs redirect_uris | Required for web applications. A list of allowed redirect URIs. Once a user completes the authentication process on Google, App Services redirects them back to either a specified redirect URI or, if no redirect URI is specified, the URL that they initiated the authentication request from. App Services will only redirect a user to a URI that exactly matches an entry in this list, including the protocol and any trailing slashes. | |
Domain Restrictions domain_restrictions | Optional. A list of approved domains for user accounts. If specified, the provider checks the domain of a user's primary email address on Google and only allows them to authenticate if the domain matches an entry in this list. For example, if NoteIf you've specified any domain restrictions, you must also require the email address field in the Metadata Fields setting. | |
OpenID Connect config.openId | Optional. Default If ImportantOpenID Connect Support Varies by SDKRefer to SDK-specific documentation about support for OpenID Connect. Not all SDK implementations of Google Authentication support OpenID Connect, while others require it. NoteOpenID Connect Does Not Support Metadata FieldsGoogle supports OpenID as part of their OAuth 2.0 implementation but does not provide access to restricted scopes for OpenID authentication. This means that App Services cannot access metadata fields for users authenticated with OpenID Connect. |
Examples
For code examples that demonstrate how to register and log in using Google authentication, see the documentation for the Realm SDKs: