MongoDB Shell 에 오신 것을mongosh 환영합니다()
MongoDB Shell인 mongosh는 Atlas, 로컬 또는 다른 원격 호스트에서 MongoDB 배포와 상호 작용하기 위한 JavaScript 및 Node.js REPL 환경입니다. MongoDB Shell을 사용하여 쿼리를 테스트하고 MongoDB database의 데이터와 상호 작용할 수 있습니다.
_Spot.webp)
셸에서 MongoDB 액세스하기
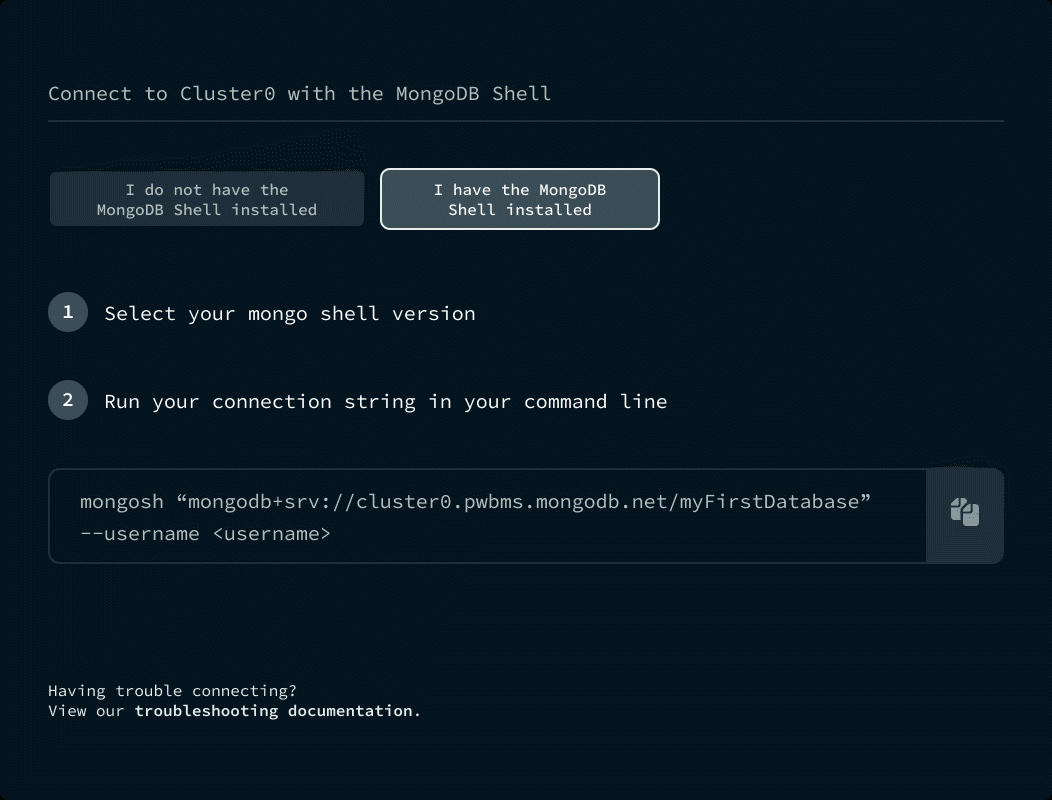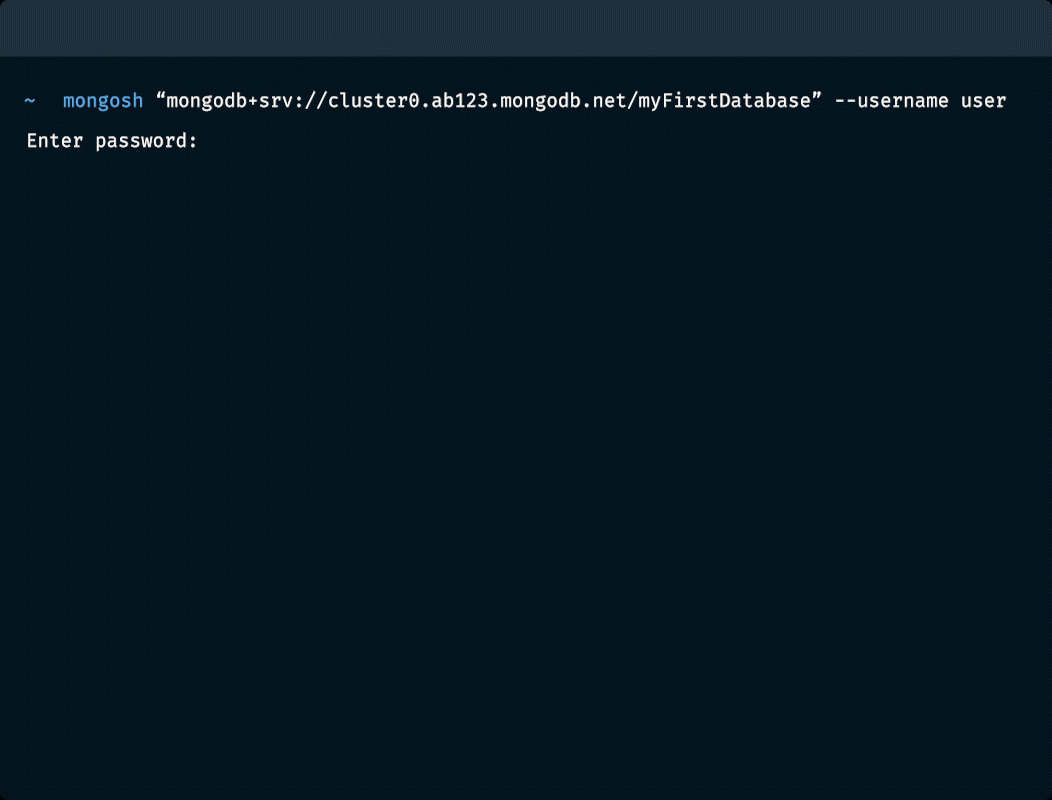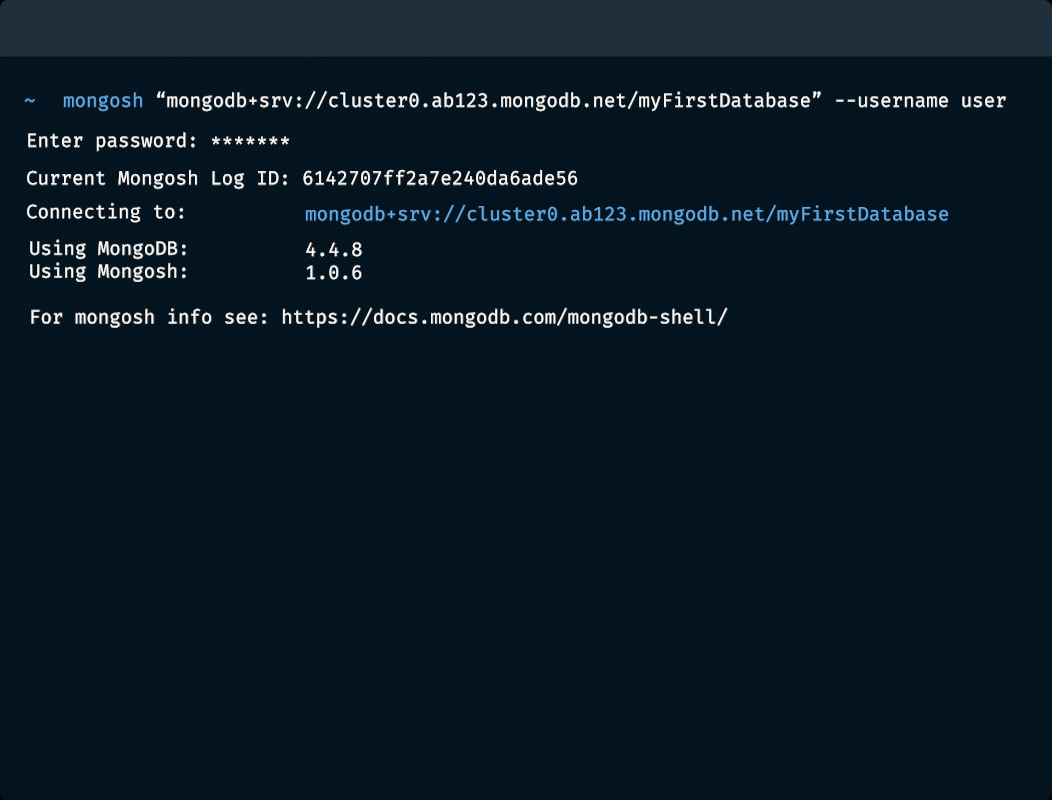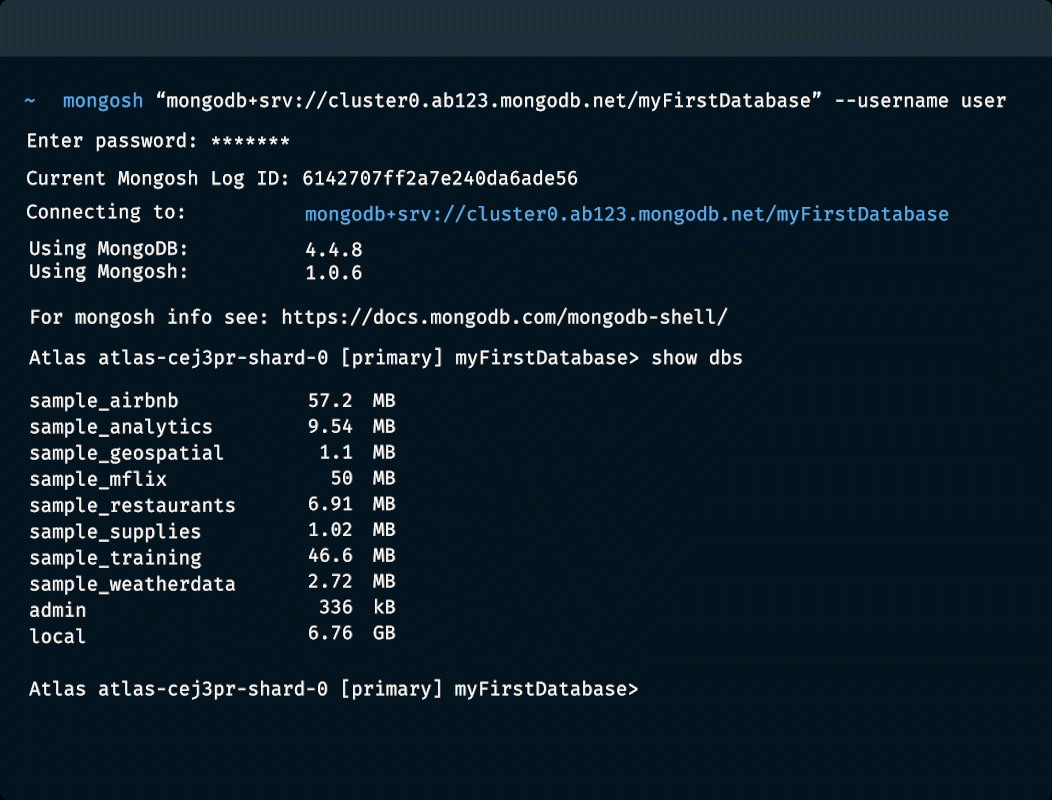
문서 삽입
mongosh 다음을 포함한 일반적인 삽입 작업을 지원합니다.
자세한 내용 및 예제는 문서 삽입을 참조하세요.
문서 읽기
db.collection.find() 메서드를 사용하여 컬렉션의 문서를 쿼리합니다. 자세한 내용과 예시는 쿼리 문서를 참조하세요.
문서 업데이트
mongosh 다음을 포함한 일반적인 업데이트 작업을 지원합니다.
자세한 내용 및 예제는 문서 업데이트를 참조하세요.
문서 삭제
mongosh 다음을 포함한 일반적인 삭제 작업을 지원합니다.
자세한 내용 및 예시는 문서 삭제를 참조하세요.
집계 파이프라인 실행
db.collection.aggregate() 메서드를 사용하여 mongosh에서 집계 파이프라인을 실행할 수 있습니다. 집계 파이프라인은 지정한 단계에 따라 문서를 집계된 결과로 변환합니다. 자세한 내용과 예시는 집계 파이프라인 실행을 참조하세요.
데이터베이스 및 컬렉션 관리
shell에서 데이터베이스에 대한 정보를 보고, collection 또는 뷰를 만들고, 데이터베이스를 삭제하는 등 이 모든 작업을 shell에서 수행할 수 있습니다. 모든 데이터베이스 메서드보기
collection 메서드를 사용하여 collection 작업을 수행하고, 인덱스를 생성 또는 삭제하고, queries를 설명합니다.
_Spot.webp)
CRUD 또는 관리 작업에 대한 스크립트 실행
MongoDB에서 CRUD 또는 관리 작업을 수행하는 MongoDB Shell로 실행할 스크립트를 작성합니다.
예를 들어 개발 또는 스테이징 환경에서 합성 또는 모의 데이터를 MongoDB에 시드하는 JavaScript 파일이 있는 경우 다음을 사용하여 파일을 실행합니다.
mongosh YOUR_JS_FILENAME.js
JavaScript와 함께 MongoDB Shell을 사용하여 MongoDB: 스크립트 쓰기에 액세스하는 튜토리얼을 살펴보세요.
.mongoshrc로 사용자 지정 헬퍼 함수 만들기
shell에 대규모 헬퍼 함수를 반복해서 작성하시나요? .mongoshrc 구성 파일 에 저장합니다. 예를 들어, 쿼리를 위해 날짜 문자열을 ISO 형식으로 변환하는 경우가 자주 발생하는 경우 .mongoshrc 에서 이를 처리하는 함수를 만듭니다.
function toISO(dateString) { return new Date(dateString).toISOString(); }
그런 다음 mongosh 에서 함수를 호출합니다.
db.clientConnections.find( { connectTime: toISO("06/07/2017") } )
자세한 내용 은 구성 파일에서 코드 실행을 참조하세요.
스니펫 사용 또는 게시
편리하게 재사용할 수 있도록 기존 스니펫 을 코드베이스로 가져옵니다. 또는 사용자 지정 사용 사례에 맞는 스니펫을 만들고 공유할 수도 있습니다.
예를 들어, 크론 작업으로 매일 가져오는 데이터의 유효성을 검사하는 스니펫이 있을 수 있습니다. 개발팀이 액세스할 수 있도록 이 스니펫을 게시할 수 있습니다. 커뮤니티 레지스트리에 게시하거나 비공개 레지스트리를 구성합니다.
자세한 내용은 레지스트리 및 레지스트리 구성을 참조하세요.
_Spot.webp)
기타 강력한 기능
외장 또는 내장 편집기를 이용해 여러 줄 기능을 사용할 수 있습니다. 줄 중심의 mongosh 기본 콘솔을 뛰어넘습니다.
지난 30일 이내의 모든 세션에 대한 로그에 액세스합니다. 정확히 기억나지 않는 명령 구문이나 스크립트로 작성할 수 있는 일반적인 명령을 찾을 수 있습니다.
mongosh가 지원하는 메서드를 확인할 수 있습니다. 지원되는 메서드에 대한 예시 구문 및 매개변수 상세 정보를 확인 가능합니다.