MongoDB released one of the most anticipated features of Client-Side Field Level Encryption (FLE): Client-Side FLE support for any KMIP-compliant key provider.
Client-Side FLE delivers the strongest privacy and security controls. MongoDB drivers encrypt the sensitive fields in your documents before they leave the application. Client-Side FLE allows customers to:
Protect data while being transmitted, at rest and in use. The database never sees plaintext, but data remains queryable.
Make data unreadable to anyone running the database for you, or who has access to the underlying database infrastructure
Simplify the process of enforcing right to erasure (sometimes called right to be forgotten) mandates in modern privacy regulations such as the GDPR or the CCPA. This is because you simply destroy the key encrypting a user’s PII, and their data is rendered unreadable and unrecoverable — in memory, at rest, in backups, and in logs
KMIP is a standardized protocol that allows services and applications to perform cryptographic operations such as key management, certificate signing, encryption and more. KMIP defines how key management operations and data should be exchanged between client and servers. Now, MongoDB Client-Side Field Level Encryption supports any KMIP-enabled key provider, so customers can benefit in the following ways:
Customers can use any key provider that is KMIP-enabled, in addition to the key management services provided by major cloud providers like AWS, Google Cloud, and Azure.
Customers can use their own custom in-house key management solution that is KMIP-enabled.
The following is the illustration of the query flow submitted by an authenticated client using FLE.
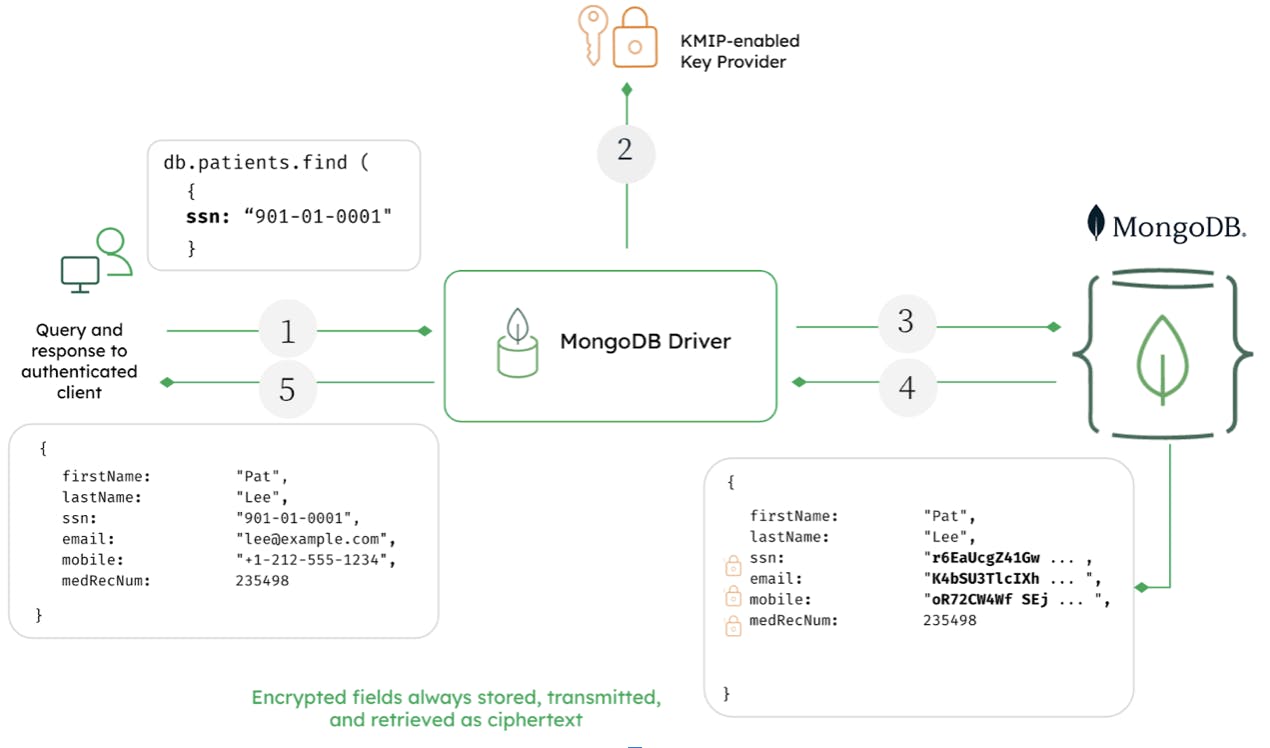
In this example let us assume we are retrieving a user’s record by their SSN number:
When the application submits the query, the MongoDB driver first analyzes it to determine if any encrypted fields are involved in the filter.
Recognizing that the query is against an encrypted field, the driver requests the key encryption key from the KMIP-enabled key provider. The key provider returns the keys to the MongoDB driver and encrypts the key fields such as SSN # in this example.
The driver submits the query to the MongoDB server with the encrypted fields rendered as ciphertext.
The MongoDB server returns the encrypted results of the query to the driver.
The query results are decrypted with the keys held by the driver, and returned to the authenticated client as readable plaintext.
For more information on Field Level Encryption and Atlas Security Controls, refer to the following resources: